- TSCM teams
- Cyber security departments
Liked what we do?
Please message us with any questions you might have
Contact us
A powerful, phone-based toolkit for WiFi connection manipulation and analysis.
Manipulate, analyze, and extract intelligence from Wi-Fi networks with a single smartphone-based device – Wi-Fi Hunter. The built-in, advanced detection algorithms allow cybersecurity teams to proactively detect any intrusion attempts into their network or presence of Wi-Fi monitoring systems and, subsequently, localize it. Wi-Fi Hunter’s ability to detect and locate hidden access points or Wi-Fi enabled devices will benefit TSCM teams. The built-in deauthentication capability prevents Wi-Fi devices from using the selected Wi-Fi network. It can be useful whether the target is an unwanted intruder into your network, or you are looking to block him from using Wi-Fi to intercept his communications via another channel (such as cellular). Wi-Fi Hunter also provides deeper insights into the surrounding Wi-Fi landscape – it collects detailed information about all Wi-Fi enabled devices in proximity, as well as handshakes and probe requests.
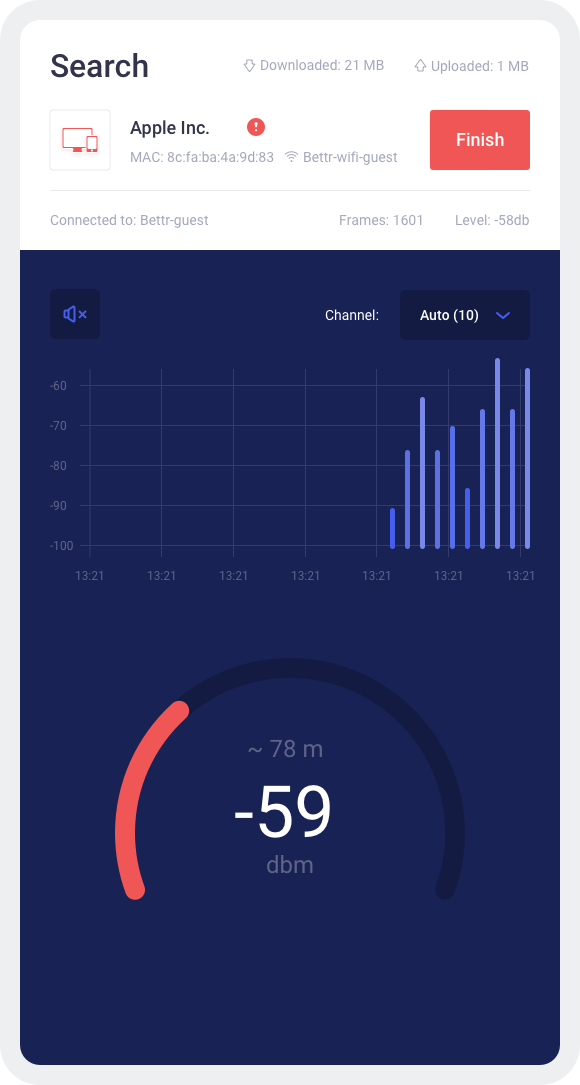
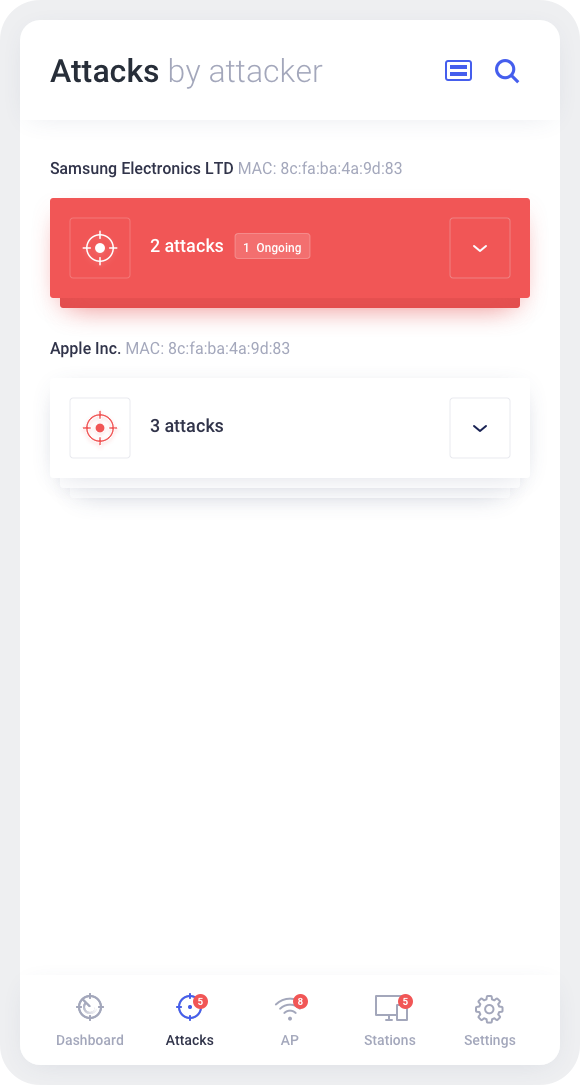
Features:
Contact us